Security is always top-of-mind, with the recent pandemic the need to focus on security-first becomes top priority. We currently are applying Data Science methods to go on the offensive to weave a creative solution with partners in the Cybersecurity field of study. Our goal is to develop an Hyperautomation Security software solution driven by Automated Artificial Intelligence (AutoAI), Automated Machine Learning (AutoML) that makes use of dynamic autonomous features that are pre-configured, fully managed, simply deployed, and in a secure environment.
- Self-Driving
All security management, integrated monitoring intelligence, and tuning processes are all automated. CISOs can now focus on more important tasks, including aggregation, modeling, processing, governance strategies, and helping secure developers vulnerabilities with minimal changes to their application code. - Self-Securing
Built-in capabilities protect against both external attacks, malicious packages, and internal users. This helps eliminate concerns about cyberattacks on unpatched or unencrypted databases. - Self-Repairing
This can prevent downtime, including unplanned maintenance, and swapping out vendors. An autonomous requires only a few minutes of downtime per month, including patching or swapping.
This provides many benefits…
- Auto-Provisioning
Automatically deploys mission-critical security defenses that are fault-tolerant and highly available. Enables seamless scale-out, protection in case of a server failure, and allows updates to be applied in a rolling fashion while applications continue to run. - Auto-Configuration
Automatically configures the security defenses to optimize for specific workloads. Everything from the memory configuration, the formats, and access structures are optimized to improve performance. Customers can simply load data and go. - Auto-Indexing
Automatically monitors workload and detects missing indexes that could accelerate applications. It validates each index to ensure its benefit before implementing it and uses machine learning to learn from its own mistakes. - Auto-Scaling
Automatically scales compute resources when needed by workload. All scaling occurs online while the application continuously runs. Enables true pay per use. - Automated Data Protection
Automatically protects sensitive and regulated data in the database, all via a unified management console. Assesses the security of your configuration, users, sensitive data, and unusual activities. - Automated Security
Automatic encryption for the entire database, backups, and all network connections. No access to OS or admin privileges prevents phishing attacks. Protects the system from both cloud operations and any malicious internal users. - Auto-Backups
Automatic daily backup of data or on-demand. Restores or recovers a data to any point in time you specify in the last 60 days. - Auto-Patching
Automatically patches or upgrades with zero downtime. Applications continue to run as patching occurs in a round-robin fashion across cluster nodes or servers. - Automated Detection and Resolution
Using pattern recognition, hardware failures are automatically predicted without long timeouts. IOs are immediately redirected around unhealthy devices to avoid hangs. Continuous monitoring automatically generates service requests for any deviation. - Automatic Fail-over
Automatic fail-over with zero-data loss to standby. It’s completely transparent to end-user applications. Provides 99.995% SLA.
By placing this knowledge into a Data Warehouse, this critical information can be analyzed, then apply real-time algorithms via data science to eliminate a cyber-criminals attack plan before they get started.
There are some simple steps that any organization or individual can take to isolate, reduce, or eliminate the attack plane. There are hundreds of Cybersecurity firms. We will see which ones are the most helpful in your specific environment. Use advanced security encryption, false-masks, to protect your data or databases against external attacks, data breaches, and internal misuse of information.
Multi-layer Defense. Remember protect who gets within your walls. Utilize universal multi-factor authentication (MFA), a broad spectrum Identify Access Management (IAM), and Identify Governance Administration (IGA) at the center of Business Process Automation to always provide the optimal defense to best prevent a cyberattacks.
If one of your systems is encamped or infected with malware, your network is quickly compromised; your data has been stolen and shared with other criminals; your backups have been corrupted; now they can encrypt your data and ask you to pay!
Your business has many attack planes for infection. You need to be able to predict, prevent, protect, and remediate instantly if threat actors attempt to gain entry to disrupt, control or destroy your ability to operate as a business. Protection of each end-point, segment, and every fabric of your business – IoT devicse, industrial controls, 3rd party devices, independent software solution, your workforce, and much more.
Zero-Trust Approach. Protects against advanced threats, identifying activity patterns, automating security controls, and providing isolated network virtualization. We need to operate with Zero-Trust Security, move our fences around, change the game and keep would be attack planes shifting. We need to go on the defensive with so many vulnerabilities exposed – we failed by operating as if we had trusted users. Trust is not even earned because stolen identity complicates zero-trust we need to deploy other methods to verify the identity of users.
Real-time Continuous Diagnostics and Mitigation (CDM) that protects threats in the Control Plane and Asset Plane!
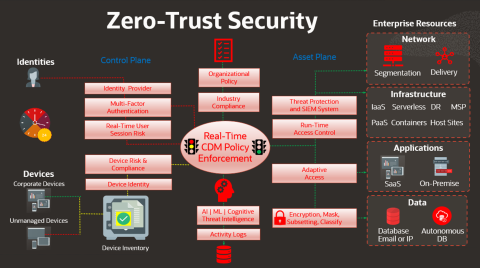
We need to implement proper security controls, change all logins, passwords and move to zero tolerance immediately! The Trojan horses are sitting inside our systems… we have been exposed too long and the enemy is within our walls. Our last line of defense is placement of security around our assets.
It’s not who is trying to access but from where? We need to fingerprint, facial recognize, analyze the trusted users to validate their identity before access is granted. We need to follow that user like a trail of bread crumbs within the system to see if they are performing as normal or trying to gain access to unauthorized applications, data or applications.
Build Advanced Protection
It is a requirement these days to incorporate advanced analytical methodologies, AI & ML capabilities, security features to reduce your operational risks, reduce alert fatigue, and encompasses separate yet symbiotic functionalities, including a 360° dashboard for data visualization; adaptive intelligence and analytics for dynamic risk assessments. Knowing you have peace-of-mind in the workplace, and all the facets that it interfaces with daily – have risk protection and that your applications are protected from all malicious activity with a security-first knowledge.
Service-Level Agreements (SLAs)
An SLA is a contract that includes the list of services and highlights the quality standards that the provider should follow to guarantee customer satisfaction. The contract also recalls the ways to redress gaps and problems that are foreseen and unforeseen. An SLA is an integral part of any IT vendor contract. It pulls together information about offered services and customer expectations.
There is no silver-bullet for Cybersecurity but Risk Mitigation allows us to be more diligent and responsible with regards to having SLA around specific metrics like application availability, automated patch management, penetration testing, rotation of security tools, company training around (security, business e-mail compromise, zero-trust, etc.), categorization of systems based upon (risk, vulnerability, business loss prevention, business impacts), planned and unplanned outages.
The Glass House
Recent Gartner research shows that 88% of boards regard cybersecurity as a business risk rather than solely a technical IT problem. Some boards have responded to this by instituting cybersecurity-specific committees overseen by a dedicated director.
Finally expressing concern and caution around the cybersecurity posture of the organizations with whom they are willing to conduct business. Increased investor interest, sudden public pressure, a whole new slew of employee requirements, and governmental regulations driven by unprecedented executive orders are strengthening the incentives for organizations to track and report cybersecurity goals and metrics within their environmental, social and governance (ESG) efforts as a business requirement.
Many LinkedIn published articles on security https://www.linkedin.com/search/results/content/?keywords=security%20&origin=FACETED_SEARCH&postedBy=%5B%22me%22%5D&sid=lNn

