True “business transformation” only occurs when you can create a “secured” optimal customer experience. Securing business-critical sectors, infrastructure, and facilities is challenging to say the least.
A Strong Authentication & Authorization Strategy Is Essential
Developing a sound security strategy requires protecting all critical resources with both authentication and authorization. With a strong authentication and authorization strategy in place, enterprises can consistently verify who every user is, monitor there intentions, and what they have access to do—preventing unauthorized activity that poses a serious threat. By ensuring all users properly identify themselves and access only the segmented resources they need, an organization can maximize productivity, strengthen their security to prevent breaches that try to ransom their businesses parting them of their revenue and their reputation.
Secure facilities require strict end-user authentication prior to accessing environments, this means a user must be “fully vetted” this means authentic, authorized, and has access to minimal set of attributes and applications.
| Authentication | Authorization |
| Of the same origin as claimed; genuine | To grant permission or power necessary to do (something) |
| Authentication verifies who the user is. | Authorization determines what resources a user can access. |
| Authentication works through MFA, passwords, one-time pins, bio-metric or GPS information, and other information provided or entered by the user. | Authorization works through a series of qualifying questions and settings that are implemented and maintained by the organization. |
| Authentication is the first step of a good identity and access management process. | Authorization always takes place after authentication. |
| Authentication is visible to and partially changeable by the user. | Authorization isn’t visible to or changeable by the user. |
| Example: By verifying their identity end-users can then are routed to what then have authority to access part of a multi-stage vetting process to finally gain access to an fully scanned applications that are secure. | Example: Once their level of access is authorized and governance access determined then different levels of application access based on the permissions set by the organization. |
To insure “no imposters are present, with simple validation to then provide effective and efficient communication. This automation that validates your identity, what you can have access to is the “governance process” that must occur prior to accessing any secured applications.
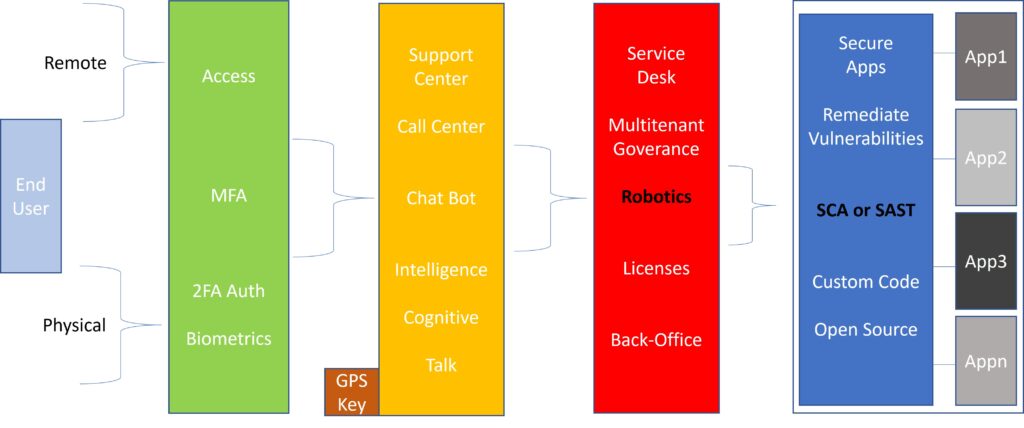
We have partnered with leading security solutions to eliminate global threats, making a positive impact on cybersecurity, from individual users to globe-spanning organizations.
As you know, a universal MFA platform, only strict network segmentation solution, and digital asset encryption can prevent cyber-attacks on-premises and in cloud deployments. We have added additional defensive layers of universal authentication, verification, and remediation to strengthen defense layers: intelligent chat bot, streamlined robotic governance, and finally application cleansing software composition analysis to ensure an optimal end-user experience.
____________________________________________________
Are you interested in finding out more how a universal MFA platform can prevent 99.9% of cyber-attacks?
Multi-factor Authentication (MFA), this is a universal MFA, providing outstanding expertise, support, and training. Works in the Cloud (public/private), hybrid, on-premises, embedded, air-gap, shop-floor, mobile, FaaS, SCIFs, SCAFs, OT, or IoT. Authentication with any user, anywhere, any device, and on any authenticator.
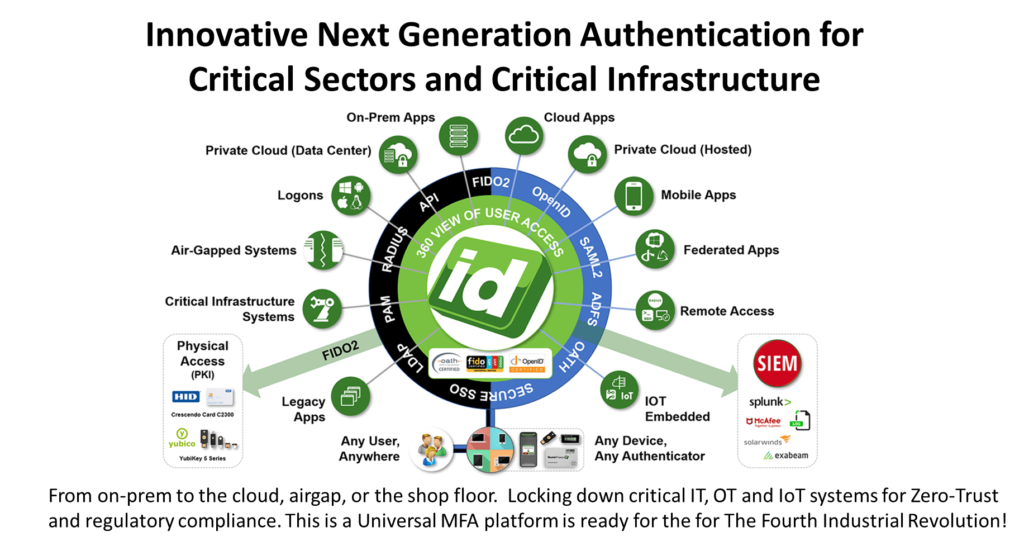
Open authentication standards FIDO2, OATH, OpenID, SAML2, ADFS, Secure SSO, LDAP, PAM, RADIUS or APIs. Converged credentials FIDO2 with top PKI, integrates with SIEM leaders. Can authenticate offline without Internet locking down critical IT, OT and IoT systems for Zero-Trust and regulatory compliance.
The most complete MFA Solution
____________________________________________________
Would you like to find out more on how to transform your customers into world class, connected experiences that meet and exceed their human needs?
Intelligent Cognitive Chat-Bot. Our goal is to simply introduce you to effective and efficient communications. We can transform your call center operations by significantly reducing or deflecting the calls from human agents in the call center.
The solution we’re referring to can strengthen security, increase stickiness, loyalty, lifetime value, transform your Customer Experience (CX), increase engagement through hyper-personalized interactions 24×7 knowing an outreaches past call history, their preferences, their current context, and their current goals.
An intelligent cognitive chat-bot!
____________________________________________________
How do you streamline an organizations workforce while reducing IT staff requirements with simple clean automation that provides a safe secure working environment?
Automation Can Reduce Your Security Risk, the management and governance of user identification strategies has always been an important concept for business leaders. Knowing how to ensure your administration, access, and efforts remain as secure as possible is crucial to keeping your company secure.
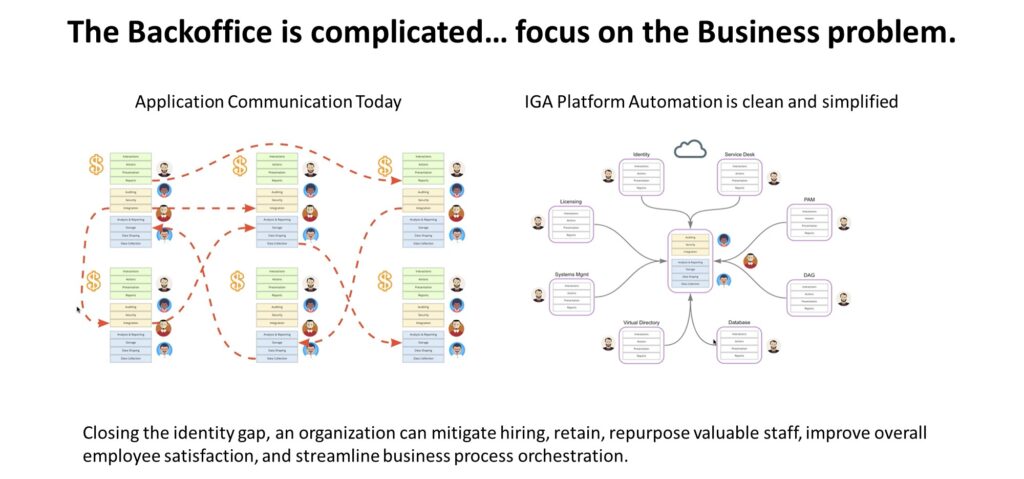
As criminal activities have evolved, so to have our approaches to streamline identity governance and administration needs to move at the speed of light. Companies continue to embrace the concept of hybrid and remote work, and teams log into cloud software from multiple locations, identity governance is increasingly crucial.
Reducing the back office complexity with robotic automation!
____________________________________________________
Security has always been a challenge building security-first into your applications, so you need to just focus on coding?
Software Composition Analysis (SCA), is an automated process that identifies the open source software in a codebase. This analysis is performed to evaluate security, license compliance, and code quality. AppSec has become one of the hottest buzzwords in the DevOps ecosystem over the past couple of years. It means building security into requirements, into the design, the code, and the deployment stages — in short, it’s a strategy extends DevOps efficiencies to software security.
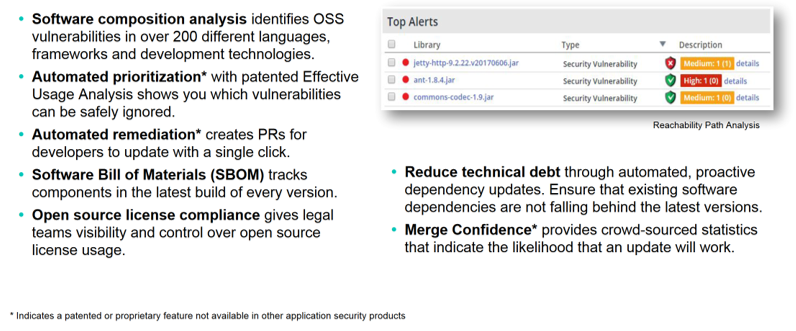
Implementing DevSecOps requires you to perform a broad evaluation of your existing IT resources and DevOps processes, then build a holistic strategy that integrates stronger security into all of them.

